- Copy internal post link
- Copy external post link
- Report article
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html
[content:5756708730]
Mikrotik hinter Fritz, Wireguard Site to Site, keine Verbindung
mit hilfe von Aqui habe ich bereits eine funktionierende IPSec Verbindung konfiguriert. Nun kommt die Neugier und der Upgradetrieb dazu und hat das Setup wie folgt erweitert:
Ziel Site to Site Verbindung:
Büro
Fest IP 37.xx.xx.xx
192.168.0.1 Fritz
192.168.0.15 Mikrotik Hex
192.168.0.230 Mikrotik Hex
nach
Zuhause
DSL Light
192.168.178.1 Fritz
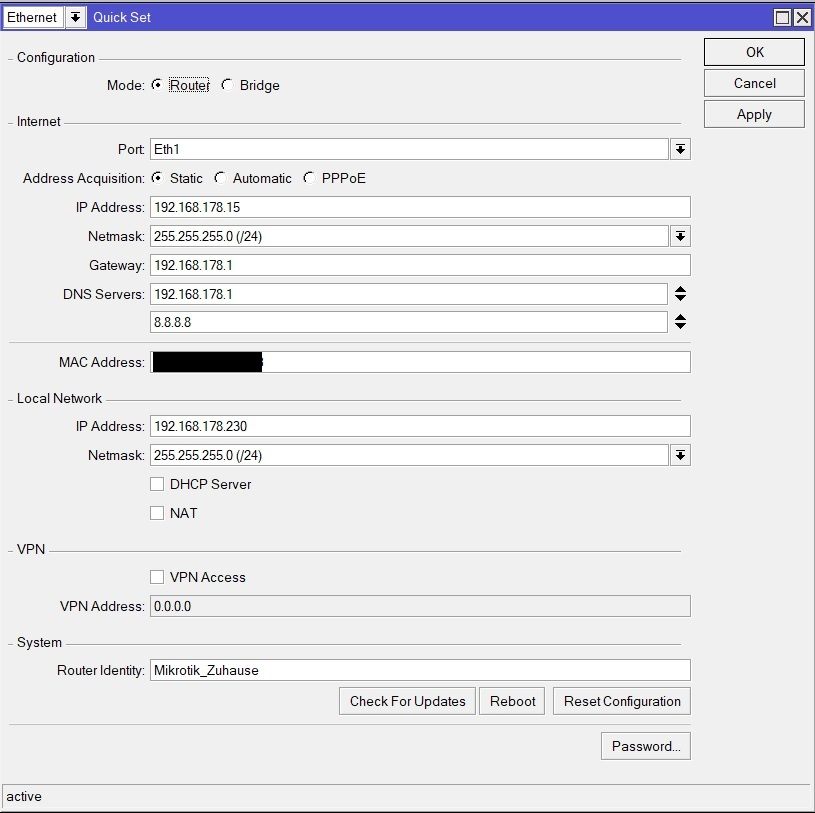
192.168.178.15 Mikrotik RB2011
192.168.178.230 Mikrotik RB2011
als Tunnel habe ich die IP aus dem Forum gewählt: 100.64.64.0
Die Mikrotiks sind mit dem Port 1 direkt an der Fritz und mit einem anderen Port am Switch.
In beiden Fritzboxen habe ich den Port 51820 freigeschaltet:
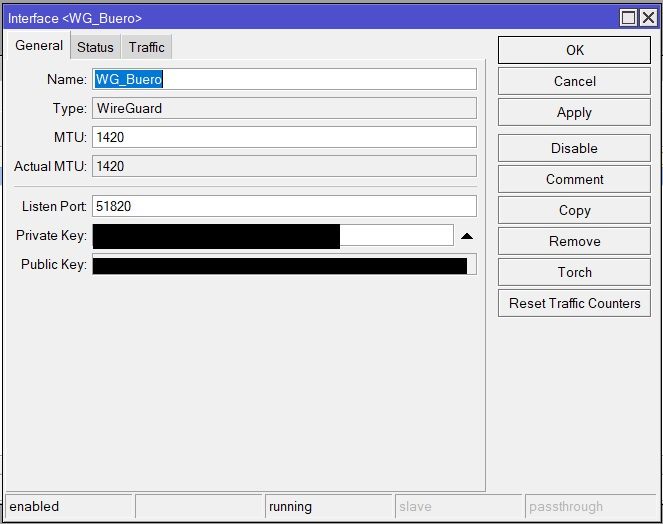
und die Mikrotiks lt. Anleitung konfiguriert:
Die Adressen auf beiden Mikrotiks hinterlegt:
Die Routen angelegt:
und die Firewall freigeschaltet:
Und war nun der Meinung mich an den diversen Anleitungen im Forum ans Ziel gearbeitet zu haben... Aber leider tut sich nichts, keine Verbindung und im Log wird nichts angezeigt. Also kein Fehler, an welcher Stelle es klemmt.
Nun steh ich wieder auf dem Schlauch und weiss nicht, an welcher Stelle anpacken zu müssen.
Content-Key: 5756708730
Url: https://administrator.de/contentid/5756708730
Printed on: May 6, 2024 at 17:05 o'clock
- Comment overview - Please log in
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5757202162
[content:5756708730#5757202162]
[admin@Mikrotik_Zuhause] > export
# jan/31/2023 17:04:24 by RouterOS 7.7
# software id = HT0D-UHE9
#
# model = RB2011UiAS
# serial number = xxxxxxxx
/interface bridge
add admin-mac=18:FD:74:F8:5E:CC auto-mac=no comment=defconf name=bridge
/interface wireguard
add listen-port=51820 mtu=1420 name=WG_zuhaus
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=default-dhcp ranges=192.168.88.10-192.168.88.254
/ip dhcp-server
add address-pool=default-dhcp disabled=yes interface=bridge name=defconf
/port
set 0 name=serial0
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=ether6
add bridge=bridge comment=defconf interface=ether7
add bridge=bridge comment=defconf interface=ether8
add bridge=bridge comment=defconf interface=ether9
add bridge=bridge comment=defconf interface=ether10
add bridge=bridge comment=defconf interface=sfp1
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
/interface wireguard peers
add allowed-address=100.64.64.0/24,192.168.0.0/32 endpoint-address=\
xxbueroxx.myfritz.net endpoint-port=51820 interface=WG_zuhaus \
persistent-keepalive=25s public-key=\
"xxxx"
/ip address
add address=192.168.178.230/24 comment=defconf interface=bridge network=\
192.168.178.0
add address=100.64.64.0/24 interface=WG_zuhaus network=100.64.64.0
/ip dhcp-client
add comment=defconf disabled=yes interface=ether1
add comment=defconf disabled=yes interface=ether1
/ip dhcp-server network
add address=192.168.178.0/24 comment=defconf dns-server=192.168.178.230 \
gateway=192.168.178.230 netmask=24
/ip dns
set allow-remote-requests=yes servers=192.168.178.1,8.8.8.8
/ip dns static
add address=192.168.178.230 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=accept chain=input dst-port=51820 in-interface=WG_zuhaus protocol=\
udp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=accept chain=input dst-port=51820 in-interface=WG_zuhaus protocol=\
udp
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" disabled=yes \
ipsec-policy=out,none out-interface-list=WAN
add action=masquerade chain=srcnat comment="defconf: masquerade" disabled=yes \
ipsec-policy=out,none out-interface-list=WAN
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=Mikrotik_Zuhause
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN
[admin@Mikrotik_Zuhause] >- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5757246310
[content:5756708730#5757246310]
[admin@Mikrotik_Buero] > export
# jan/31/2023 17:09:13 by RouterOS 7.7
# software id = WZ23-IZ38
#
# model = RB750Gr3
# serial number = xxxxxxx
/interface bridge
add admin-mac=18:FD:74:75:99:8C auto-mac=no comment=defconf name=bridge
/interface wireguard
add listen-port=51820 mtu=1420 name=WG_Buero
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=default-dhcp ranges=192.168.88.10-192.168.88.254
/ip dhcp-server
add address-pool=default-dhcp disabled=yes interface=bridge name=defconf
/port
set 0 name=serial0
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
/interface wireguard peers
add allowed-address=100.64.64.0/24,192.168.178.0/32 endpoint-address=\
xxzuhausexx.myfritz.net endpoint-port=51820 interface=WG_Buero \
persistent-keepalive=25s public-key=\
"xxxx"
/ip address
add address=192.168.0.230/24 comment=defconf interface=bridge network=\
192.168.0.0
add address=100.64.64.0/24 interface=WG_Buero network=100.64.64.0
/ip dhcp-client
add comment=defconf disabled=yes interface=ether1
add comment=defconf disabled=yes interface=ether1
/ip dhcp-server network
add address=192.168.0.0/24 comment=defconf dns-server=192.168.0.230 gateway=\
192.168.0.230 netmask=24
/ip dns
set allow-remote-requests=yes servers=192.168.0.1,8.8.8.8
/ip dns static
add address=192.168.0.230 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=accept chain=input dst-port=51820 in-interface=WG_Buero protocol=\
udp
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=accept chain=input dst-port=51820 in-interface=WG_Buero protocol=\
udp
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" disabled=yes \
ipsec-policy=out,none out-interface-list=WAN
add action=masquerade chain=srcnat comment="defconf: masquerade" disabled=yes \
ipsec-policy=out,none out-interface-list=WAN
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
/system clock
set time-zone-name=Europe/Berlin
/system identity
set name=Mikrotik_Buero
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN
[admin@Mikrotik_Buero] >- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5757271737
[content:5756708730#5757271737]
wenn du bei deinen MikroTiks auf der WAN und LAN Seite den selben IP Adressbereich hast, kannst du die beiden Geräte gleich als Bridge konfigurieren und nicht als Router, dann brauchst du auch keine Firewallregeln.
SG
Edit: auf der Büroseite brauchst du keinen Endpoint konfigurieren. Mir haben die YouTube Videos von „The Network Berg“ geholfen, kann ich dir nur empfehlen 😉
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5757302260
[content:5756708730#5757302260]
danke für Deine schnelle Hilfe. Ich habe das nicht "absichtlich" gemacht, sonder dachte, dass es so
richtig ist.
Was würdest Du für meine Site to Site Konfiguration mit WireGuard empfehlen?
Mikrotik als Bride?
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5757397053
[content:5756708730#5757397053]
Naja, warum nicht Fritz!box zu Fritz!box?
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5757950270
[content:5756708730#5757950270]
wie gesagt.. Fritz zu Fritz mit IPSec hatte ich am laufen...
Nun will ich Wireguard über Mikrotik hinter Fritz testen.
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5758308692
[content:5756708730#5758308692]
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5767982597
[content:5756708730#5767982597]
Mikrotik OS kennenzulernen.
Daher will ich die Mikrotikauf jeden Fall einbinden.
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5771537146
[content:5756708730#5771537146]
-> Interface List, Lan / WireGuard auf Seite Büro und Zuhause eingerichtet.
-> Adress List angepasst / 100.64.64.1/24 - 100.64.64.0 - WG Verbinundg, auf beiden Seiten
-> Firewall Regel "input" von ganz unten, nach oben geschoben, zu den andern input Regeln auf beiden Seiten.
-> Firewall neue Regel input erstellt für die 100.64.64.1 - WG Adresse auf beiden Seiten + hochgeschoben.
-> Firewall neue Regel, !Forward für 100.64.64.0/24 an WG + Out Interface Bridge auf beiden Seiten + hochgeschoben
-> Firewall neue Regel, Forward WG -> Ether 1 auf beiden Seiten + hochgeschoben
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5781439591
[content:5756708730#5781439591]
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5790878219
[content:5756708730#5790878219]
Oder wie liest man das Protokoll von WireGuard über Mikrotik aus? Dass würde
sicherlich auch weiterhelfen.
Im normalen Log steht nur... Message WG_Buero link up
Keine weitere Medlung welche auf den Fehler hinweissen könnte.

- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5790970673
[content:5756708730#5790970673]
Des weiteren verwendest du einen für CGNat reservierten Adressbereich 100.64.0.0/10.
Ich würde dir erst mal die Grundlagen zur IP-Adressierung empfehlen bevor du mit Wireguard losrennst.
/interface wireguard peers
add allowed-address=10.20.0.1/32,192.168.0.0/24 endpoint-address=\
xxbueroxx.myfritz.net endpoint-port=51820 interface=WG_zuhaus \
persistent-keepalive=25s public-key=\
"xxxx"
/ip address
add address=10.20.0.2/24 interface=WG_zuhaus network=10.20.0.0/interface wireguard peers
add allowed-address=10.20.0.2/32,192.168.178.0/24 endpoint-address=\
xxzuhausexx.myfritz.net endpoint-port=51820 interface=WG_Buero \
persistent-keepalive=25s public-key=\
"xxxx"
/ip address
add address=10.20.0.1/24 interface=WG_Buero network=10.20.0.0Und dann in der Firewall natürlich die Forward-Chain für Wireguard freischalten
/ip firewall filter add chain=forward place-before=0 dst-address=192.168.0.0/24 action=accept
/ip firewall filter add chain=forward place-before=0 src-address=192.168.0.0/24 action=accept/ip firewall filter add chain=forward place-before=0 dst-address=192.168.178.0/24 action=accept
/ip firewall filter add chain=forward place-before=0 src-address=192.168.178.0/24 action=acceptDes weiteren brauchst du natürlich auch zwei Routen
Auf dem Heimrouter eine Route ins Büro Netz
/ip route add dst-address=192.168.0.0/24 gateway=10.20.0.1Auf dem Buero Router eine Route ins Heimnetz
/ip route add dst-address=192.168.178.0/24 gateway=10.20.0.2Gruß Wurstel
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5792373406
[content:5756708730#5792373406]
danke für die Tipps, nun kann ich wieder weitertesten.
DIe IP 100.64.64.0 hatte ich aus einer Anleitung hier gezogen, oder evtl. einfach falsch
geschaut oder interpretiert.
Ich arbeite nach. Deine Tipps beschäftigen mich wieder die ganze Nacht heute :D
Danke soweit.
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5797724539
[content:5756708730#5797724539]
https://youtu.be/P6f8Qc4EItc
Mit diesem solltest du alle Einstellungen haben 😉
- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5804513607
[content:5756708730#5804513607]

- Copy internal comment link
- Copy external comment link
- To the beginning of the comments
https://administrator.de/forum/mikrotik-hinter-fritz-wireguard-site-to-site-keine-verbindung-5756708730.html#comment-5805319693
[content:5756708730#5805319693]